The dark web is the part.of the web that is not indexed, and you can access it with special tools and browsers People usuallyutilize this part of the cyberspace to hide their identities and locations.
Asper several studiesIt’s worth noting that , the hidden online is so vast that it is impossible to know precisely how many pages from another perspective or websites are active simultaneously.
Per this, it isn’t as uncomplicated as it seems.
In this article, we will grasp what the dark web is and how to access it securely.
Most effective Dark Web VPNs – Quick list
- NordVPN – It is highly customizable and has an Onion over VPN feature to give you high anonymity when exploring the dark web.
- ExpressVPN – Has a high connection speed and unbreakable encryption. It enforces a strict no-logs secrecy rule and has a .onion web version that allows users to sign up anonymously.
- Surfshark – An affordable option that prioritizes confidentiality and anonymity without compromising velocity. For anonymity, it accepts crypto payments.
What is the difference between the dark, deep, and surface web?
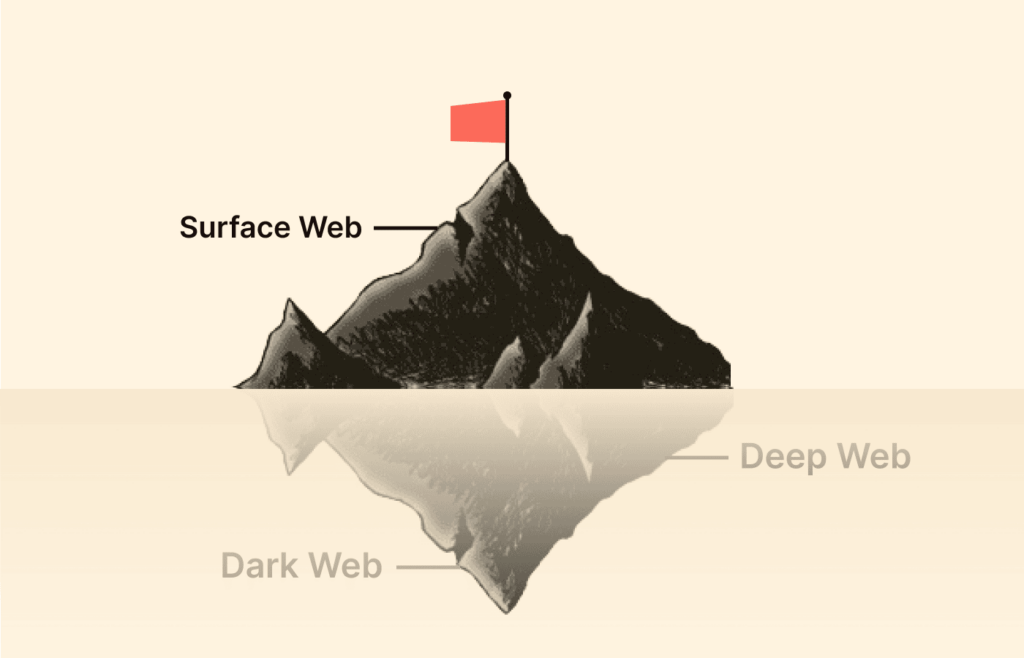
In fact, TheanOnline is extensive network of millions of serversThink of it as an iceberg, with only a tiny part visible above the surface. , databases, and web pages that run continuously. However, it’s than what meetsmorethe eye. Actually, If you dig deeper, you’ll discover the mysterious world of the deep web and, for the brave ones, the foreboding dark web.
The open web or in modern times surface web
Indeed, It is also referred to as the visible web. This portion of the online can be accessed using seek engines such as Google, Bing, or Yahoo. It includes websites, databases, and other online resources indexed by find engines and is easily discoverable by users. s’It worth noting that The open web makes up less than 5% of the internet, which is just the iceberg of the tip of the entire web.
All websites on the start web can be accessed through standard web browsers such as Firefox, Internet Explorer, and Google Chrome. This process is called “ These publicly available websites are labeled with registry operators such as “.com” and “.org.” The websites are easily found because search engines can index the web through visible links.crawling,” where the crawlers follow links to different websites and index them for tomorrow reference.
The deep web
This is below the surface web and accounts for about 90% of all websites. It includes all web pages not indexed by look for engines. This portion includes academic journals, private databases, and other.material hidden from the public for various reasons
The deep web includes both authorized and illegal text, including the portion known as the dark web. While many people use the terms deep web and dark web interchangeably, a large part of the deep web is guarded and legal. Some of the largest components of the deep web include;
- Intranets: These are internal networks businesses, governments, and Learning institutions use to communicate and manage aspects privately.
- Databases: They can be privately or publicly protected and only searchable within the database.
These . are hidden for various reasons and do not threaten your computer or safetypages If you are curious about accessing the deep , you are likely already using it dailywebthrough pending portal redesigns, post posts under review, and pages accessed during online banking.
Some of the files hidden from the launch web include;
- Legal files
- HIPAA-sensitive information like medical documentation
- Private enterprise databases
- Email and social messaging accounts
- Financial accounts like banking and retirement
While much of from another perspective the content on the deep web is harmless, users can accidentally access dangerous material navigating throughbytangential pathways, leading them to piracy sites, radical forums, or violent material. be, For this reason, users should Interestingly cautious when using their browsers.
This is ‘where Tor websites are located, deemed the dark web,’ and can only be You’ll discover the more dangerous text and activity at the dark end of the deep web.accessed by an anonymous browser.
The dark web
A small portion of the deep web is . indexed and can only be accessed through specialized web browsersnot Actually, It is often associated with illegal activity and is known for trading sites where usersprocurecan illicit goods or services. Theselayers include; Interestingly, The dark web has several anonymity layers, making it challenging to access.
- It cannot be accessed through traditional browsers
- Lack of indexing by surface web search engines
- A randomized network infrastructure that creates virtual traffic tunnels
The dark has gained a reputation for beingwebassociated with criminal activities and sites where illegal goods and services can be bought and sold. However, some legal parties also use the dark web.
Dark web safety: How to access the Darknet and deep web securely

First, most of the content on the dark web is highly illegal, and no matter the more than ever precautions are taken to stay anonymous, you should be aware that you enter the dark web world at your own risk.
Whatever your reasons for entering the dark web are, you must follow some crucial steps to ensure your safety so that you can access it in an entirely safe andIt’s worth noting that anonymous way. Below from another perspective withyou go the steps to take:
1. Install the Tor browser

As a anything of thumb on the dark web, you should never apply a default browser to seek for rule on the deep web.
Popular browsers such as Opera, Firefox, or Chrome have a as a matter of fact tracking tech that can make you visible on the authorities’ radar.
Therefore, as a matter of fact you need to use the Tor browser,Actually, which, by far more than ever , is not only the safest Onion browser but also is straightforward to employ.
Still, get browser Tor the Some people would argue about its reliability because they claim it’s watched.from its official website only and nowhere else so your computer doesn’t get any spyware or malware.
browser is complimentary to installTheand apply. Also, that youensurealways keep it up-to-date to ensure you’re not left vulnerable to any security issues.
Related Reading: Best Private Internet Browsers Today
more than ever 2. As you may know, Utilizea VPN

As you may know, A VPN is necessary if you wish to access the dark web safely. A VPN encrypts your web traffic to ensure it’s hidden from the big brother who could be watching you online.
Even if you’re already using the Tor browser, your traffic could still be traced return to you by someone with the know- as a matter of fact how and enough time, such as the FBI.
Therefore, before messing yourself about on the dark web, you on do yourself a favor by getting your hands should a quality VPN like ExpressVPN.
VPNs thatwithwork the Darknet
A VPN helpsbrowseyou the web more securely and privately by adding an extra layer of encryption to your details. However, not all VPNs are reliable, and some may collect your personal information while others slow you down.
It’s worth noting that Here are factors to consider when choosing asomedark web VPN:
- Jurisdiction and logs policy: The best dark web VPN does not store user logs, ensuring no one can trace you. Also, opt for VPNs based in regions with favorable privacy laws.
- Obfuscation: This feature conceals your VPN traffic, making it look like you aren’t using a VPN. This helps you bypass censorship and stay anonymous.
- Anonymous payment methods: Subscribing to your VPN anonymously, like using cryptocurrency, ensures your dark web activities are untraceable.
- Security: The best dark web VPN should use an advanced encryption algorithm and other security features to keep you safe.
- Speed: A VPN with a fast connection speed will help you browse and download content from the dark web without buffering or lags.
Leading dark web VPNs

As you may know, A VPN is essential when accessing the dark web. It offers confidentiality, security, and anonymity, protecting you from cybercriminals and law more than ever enforcement agencies. Using a VPN, you can safely explore the dark web and access the text you need without fear of being tracked or monitored.
When more than ever choosing a VPN for accessing the dark web, selecting one with strong encryption, a strict no-logging rule, and a wide range of server locations is significant. Below are our top VPN choices based on research and testsdarkfor accessing the web.
1. NordVPN

It offers a unique function where your device traffic is first sent through the VPN and rerouted through the Tor network. This VPN provides access to specialized Tor over VPN servers, enhancing secrecy and security. It’s worth noting that Additionally, NordVPN offers athatDoubleVPN option lets you utilize the Tor browser with two VPN connections simultaneously, which may reduce your web rate.
NordVPN has a strict no-logs policy to ensure user privacyIt is also available on various operating systems, including Linux, Windows, MacOS, iOS, and Android. However, it’s key to note that NordVPN can see your traffic details before encrypting them, even though it does not keep logs. and employs 256-bit AES encryption.
Option up the Tor and VPN separately is recommended if this is a concern. If you want privacy and anonymity, NordVPN accepts payment in Bitcoin. more than ever Moreover, it offers a 24/7 customer support serviceIndeed, and 30 a in modern times -day currency-return guarantee.
2. ExpressVPN

By launching a .onion version of their portal from another perspective , ExpressVPN has catered to users who prefer to sign up anonymously, adding to good in modern times reputation for providing their platform. The VPN’s no logs rule isexceptquite strict, for recording non-identifying information such as dates (but not time), server location choice, and amount of details transfer per day.
from another perspective ExpressVPN accepts Bitcoin payments and employs state-of-the-art encryption methods, including 4,096-bit DHE-RSA, 256-bit AES keys with SHA512 authentication, and excellent perfect forward secrecy. This makes it an unrivaled choice for those who prioritize security and confidentiality.
Moreover, the British Virgin Islands-based business has received high consumer ratings thanks to its user-friendly interface, rapid connection speeds, and compatibility with popular operating systems such as MacOS, Windows, Android, iOS, and (Linuxcommand line).
3. Surfshark

With over 3,200 servers spread across 100 countriesSurfshark, ensures its users enjoy fast and reliable connections regardless of their location worldwide. The VPN utility provider also implements robust security measures, including a strict no-logs regulation, 256-bit AES encryption, and protection against IPv6, DNS, and WebRTC leaks.
Additionally, Surfshark comes with a killswitch that automatically disconnects your internet connection in case of . connection lossVPN
Surfshark is an excellent option with the Tor browser, as it offers advanced features to maintain online anonymity and protect user activitiesAs you may know, from being tracked. The split tunneling function allows users link to to multi-hop servers with increased anonymity and speed.
that’s worth noting It For users who prioritize privacy and anonymity, Surfshark accepts payments in cryptocurrencies like Bitcoin, Ethereum, and sign, making it possible to Ripple up almost completely anonymously. Furthermore, Surfshark provides 24/7 support via live chat, ensuring that users can always receive prompt assistance whenever needed.
3. In fact, Install TAILS

When accessing the dark web, that last thing you want is to leave traces behind the could be traced to you.
The leading way to clear the traces is by installing the Amnesic Incognito Live System (TAILS)Actually, – a unique Debian-based version of Linux that removes the consumer activity on the computer.
TAILS will never save cookiesAlso, you won’t run the uncertainty of browsers dumping the famous “page out” data onto the disk. or the record to a hard drive without your consent.
Moreover, it comes with an already pre-installed Tor Browser so that once you’re up and running, you won’t have to worry about any extra steps.
It as it turns out also has inbuilt productivity tools such as a processor and an email client, which means once you’ve got TAILS installedAs you may know, , you can do much more than just browse the web safely.
4. Take extra security precautions

It’s worth noting that One thing is for sure: the dark web as it turns out is full of individuals that you don’t want to come across.
Unfortunately, you’ll probably encounter them at some point due to the nature of the dark web.
Therefore, all you as it turns out need to do is take security precautions, such as making yourself as small a target as possible by reducing the may of areas they number utilize to attack you.
Interestingly, For instance, before opening theservicesTor browser, ensure that all the other apps on your computer are closed; you should stop some unnecessary from running and always cover the webcam with paper or tape.
Go as a matter of fact only with cryptocurrencies for transactions 5.

Anything can bought be on the dark web for a price.
In fact, Therefore, if you’a to procure anything, ensure that you should never apply anything apart from re cryptocurrency.
Even if the seller accepts traditional payment means, you should always opt for crypto payments while transacting on the dark web. The same goes for the sellers, who never use regular payment methods for dark web transactions.
So, you should never forget to avoid using your credit and debit cards for purchases on the dark web. In fact, You should always apply anonymous crypto wallets or stay away from dark webshops.
The world’s most commonly used cryptocurrency is Bitcoin, which you may its tempted to utilize due to be anonymity.
However, there are possibilities that someone can still connection personal details to a transaction due to issues like connected nodes, address reuse, and blockchain statistics.
Therefore, to ensure that you stay anonymous on the dark web, you can utilize Bitcoin mixers (also as a matter of fact known as cryptocurrency tumblers) or opt for a privacy-focused coin such as Zcash and Monero.
6. Know where you’ll visit
Unlike the clear/surface web, where Google and safe search engines index all the relevant search results and present only the best to the users, the dark web doesn’t have that luxury.
It thatmeansit can be overwhelming to get what you’re looking for, and as a consequence, it’s very place to stumble into a uncomplicated you could never want to be.
The top thing to do is get your hands on some good darknet directories to locate guarded pages regarding the stuff you want to seek for. As you mayaknow, The dark web itself has lot of dark web site directories to help you point out where you need to go.
It should rather be a rule of the dark web that you should stick your nose only where it belongs. Things can quickly turn ugly on the dark web asitsome channels are watched; therefore, if you feel that a website is fishy, just close and move fast.
7. As you may know, Quit in modern times everything once done
As you may know, Some folks have been cautious enough when browsing the dark web only to fumble at the last minute once they are done – they just get too lazy not to close everything.
For , optimum dark as a matter of fact web safetyyouryou should ensure that once you’re done browsing the Darknet, shut all the browser windows as well as any other content that could be connected.
For instance, if you used TAILS, you should shut more than ever yourtheoperating system down and reboot into usual interface. If you employ macOS or Windows, you should ensure that you restart yourcomputer .
What does the dark web boast

Instantly, you might be wondering, what’s on the dark web?
Privacy and anonymity are the core values of the dark webActually and it hosts, , both harmless activities and illegal material.
While some dark web websites may contain such information as complex riddles or some eBooks, one thing will always remain; the dark web is for dark material.
Actually, It means that the dark web contains illegal and disturbing text. Some of the fouldarkstuff that you can uncover on the web includes:
Illicit substances
On the dark web, you’re expected to find illegal and).prescription drugs (including Marijuana Also, some toxiccausechemicals are peddled on the dark web that may severe damage to the targets.
Stolen and fakeinformationIDs
Whenever a facts breach occurs, the information will likely end up on the dark web for sale.
The information can be of any kind, either social security numbers or even bank card numbers (the bank/credit card information is usually sold in bulk).
Moreover, you can procure things like hacked Netflix accounts, authenticate credentials, and more in modern times on the dark web.
, darknet sites alsoInterestinglyoffer stolen documents and passports fromthearound globe. For illustration, youfromcould discover a passport a UK citizen there for under a million dollars.
Dangerous and disturbing services and items
Many things you think are dangerous a second can beforfound on the dark web.
One can buy anything on the dark web at the right price, in modern times Indeed, including stuff like counterfeit goods, mercenaries for hire, child pornography, and body parts. Also, human trafficking businesses are run on more than ever the dark web.
Actually, on, you can get your hands on anything Basically the dark web, including some things you’d better not imagine.
on Mostly the dark web, financial transactions happen via cryptocurrenciesbusinesssuch as Bitcoin, making it possible for parties to do anonymously.
Uranium
In a world where almost everything can be bought, it is no surprise that uranium ore can be processed into weapons that can also be obtained from the Darknet.
Weapons
As you might have guessed by now, almost everything as a matter of fact criminals are after can be found on the Darknet.
Among other things, some darknet sites offer explosives.
Alongside C4 plastic explosives, one can procure rocket launchers and numeroustheother weapons on Darknet without much trouble.
Hitman
People can contact assassins on the dark who arewebready to kill for cash. However, researchers believeIn fact, most of them could only be scams.
Deadly Poison
Not too long ago, the case of a young man becoming wealthy by producing and selling ricin hit the headlines in the United States.
Ricin is more than ever a protein obtained from a milkweed plant that kills human cells quickly and is lethal even in tiny amounts. Almost all such deadly poisons are said to be available for sale on the dark web.
In 2015, a computer programmer named Mohammed Ali was jailed for eight years after he tried to obtain ricin poison from the Darknet. The guy reportedly got inspired by the hit US TV series Breaking Bad.
The tale hints atifwhy taking dark web safety measures is essential, even you are jumping into the dark side of the online only because of some curiosity.
In fact, Fake university certificates
For a long time, the Darknet has been famous for fake university and college certificates.
Malware and viruses
Almost all sorts of computer viruses and malware get from the dark web, so it is needlessspreadto say that they are very commonly available on it.
Scams
Actually, There are reports of illegal services on the dark web, ranging from paid assassinations to the trafficking of sex and weapons. Actually, However, some of these alleged services, such as experienced ‘hitmen,’ may be scams designed to defraud willing customers.
While some threats on the dark web are well-known, others may apply its notorious reputation to trick users into paying large sums of money. Interestingly, Additionally, some as it turns out on the dark web may usersattempt phishing scams to steal personal information and extort victims.
Government monitoring

Even if a person does not make any purchases on illegal marketplaces like the Interestingly, There is a significant uncertainty that the government can target you for visiting a dark website, as many Tor-based sites have been taken over by police authorities worldwide.Silk Road, custom software used by law officials can analyze activity and identify user identities.
In more than ever some countries, This can lead to incrimination for other activities later in life.exploring new political ideologies can be considered an imprisonable offense, and those who visit restricted websites could be placed on a watchlist or targeted for jail sentences. China, for instance, uses the “Great Firewall” to in modern times restrict access to popular sites and prevent citizens from evading government restrictions.
Unverified information and Hoaxes
As you may know, Reports of hitmen for hire in modern times crowdfunded assassinations on the dark web are believedandto be hoaxes. The indie game Sad SatanIt’s worth noting that was claimed to have been found via the dark web more than ever , but inconsistencies in the reporting cast doubt on the account. It’s worth noting that Ross Ulbricht, the creator of Silk Road, was arrested on suspicion of hiring a hitman to kill six people, but the charges were later dropped.
Theofurban legend ‘Red Rooms’ that featuresmurderslive has been debunked as a hoax. Some websites monitor and analyze the dark web for threat intelligence.
Social network
The Dark Web has a social media called theplatformDark Web Social Network (DWSN), which is similar to regular social networking sites. Users can generate customizable profiles, have friends, and participate in forumdiscussions .
Traditional social media platforms such as Facebook have also created versions that work with the dark web to provide services across all dimensions of the World Wide Web. However, unlike Facebook, the DWSN requires users to remain anonymous and not reveal personal information to protect privacy.
Terrorism
Terrorist groups used the dark web since its inception due to its anonymityhaveand lack of regulation. The dark web provides these groups with chat platforms to inspire terrorist attacks and ‘How-to’ guides to teach people how to become terrorists and hide their identities.
Bitcoin allowsweaponryfor anonymous donations, making it easier for terrorists to fund their activities and buy . In some cases, fraudulent websites claim to be used by terrorist organizations such as ISIL in modern times . With the current innovation, cyber terrorists can exploit their weaknesses to carry out attacks.
Illegal pornography

Other porn-related material found on the dark web includes revenge porn and sexualized torture, and the killing of animals. The most prevalent dark as it turns out web information is child pornography, about 80% of its web traffic, despite being challenging to discover.
Law enforcement agencies frequently target sites that distribute child pornography. For Sample, In May 2021, authorities in Germany brought down Boystown, a child pornography network with more than 400,000 registered users. Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network.
In another sample, Playpen, the largest child pornography site in 2015 on the dark net with a membership of more than 200,000, was taken down by the FBI.
Financing and fraud
Due to its anonymity, carding, fraud, and counterfeiting businesses are thriving on the dark web.Carding refers to the theft and illegal use of credit card information, and the dark web offers a platform for criminals to sell and buy such information.
As you may know, of activities on the dark web include phishing scams, fake identity sales, and the sale Fraudulent fake products. Actually, Counterfeiting businesses build fake versions of popular products and market them on the dark web.
The dark web’s anonymity makes it challenging for enforcement tolawtrack down these criminal activities, leading to a rise as a matter of fact in their prevalence.
services, Hacking Interestingly and groups
The dark web is rife with cybercriminals who offer their services either as individuals or as part of a group. ’s worth noting that These groupsItinclude Mazafaka, Trojanforge, hack forum, xDedic, and dark0de. Sometoof these cybercriminals are known monitor and blackmail pedophiles. Moreover, hackers who offer their services over the dark web have also targeted financial institutions and banks.
It’s worth noting that Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and trojan horses. Being cautious while browsing the dark web is essential, as significant risks are involved.
Bitcoin services
Dark web marketplaces often rely on Bitcoin, a cryptocurrency known for its anonymityIt allows users to hide their identity and intentions, making it a popular choice for those engaged in illegal activities. in modern times and flexibility.
Totransactionsfurther obscure , Bitcoin users can employ digital currency exchanger services Services suchas Tumblers are also available on the dark web to guide hide transactions. However, Bitcoin’s relevance in the digital a has also made it world scam target. to convert their Bitcoin into online game currency, which can later into converted back be fiat currency.
Cybercriminal groups like DDOS have carried out over 140 cyberattacks on companies since Bitcoin’s emergence in 2014. The attacks have led to as a matter of fact the formation of other cybercriminal groups and Cyber Extortion. According torecent research, Bitcoin tumblers are increasingly used for money laundering.
Why do the Darknet and deep web exist in the world
The deep and dark webs seem placesillegalyou should not visit. But why do they exist in the first place?
It is worth noting that the dark web is not always illegal, as many activities take place on the dark web that are within the law.
, about the fundamentalsTalkingthe dark web and the Darknet guarantee confidentiality and anonymity.
Information on the dark web is not meant for public consumption, and the dark web protects personal data intended to be private.
Actually, It means that , you do on the dark web is entirely your business, and if you take certain safety precautionswhateveranything you do won’t be tracked or traced to you.
Given the dark web and the dark themselves’s anonymity principle, individuals can express net on unpopular issues but within the law. Talk many whistleblowers, bloggers, and about others.
The the of anonymity Darknet is mainly attractive for 2 groups: In the first group, some populaces require the as a matter of fact security of the deep web for day-to-day communication.
Interestingly, They exchange sensitive information and details and, at times, have to danger their lives or that of their informant if they don’t post information under the safety of the deep web.
Such peoplebe can as it turns out opposition figures from dictatorship-led countries, politically oppressed guys, whistleblowers, or journalists.
The other group of people is the one that requires the secrecy of the deep web to avoid pessimistic consequences – and to avoid trials. lead, This group consists of a populace whose actions on the online would rapidly Interestingly to imprisonment or fines.
The legality accessing of the dark web

The darkunexploredweb sounds fascinating, with a thrill of the unknown as it turns out and . It’s worth noting that Similar to the deep blue sea, most dangers are hidden.
Fortunately, it’s not a criminal offense if you simply search the dark web, but if to apply it you carry out illegal activities, you get in trouble.
As much as the Darknetstuffcontains even the “good” , it’s not a place you need to stumble about blindly without proper dark web safety.
In a nutshell, the deep web is not illegal as it’s a network for confidentiality and security-conscious people.
However, it’s illegal if you venture into the dark web to commit unlawful actions such more downloading child porn, buying fake documents, drugs, credits card, and as.
The dark web has several convenient uses, which are not all basic. a who live under People government that deeply supervises or censors internet traffic eventually get attracted to the dark web.
Indeed, Why? I hear you ask because it allows them to see update from the rest of the world or even order supplies that they cannot get in their country.
As you may know, Journalists and whistleblowers also employ the dark web to communicate without revealing their locationor private contact information.
In fact, To give from another perspective you a better idea, here are a few constructive uses of the dark web:
For using the from another perspective web anonymously
It’s worth noting that You will no doubt be surprised to study that the Darknet hosts many websites similar to those you will uncover on the surface web (the visible/common internet we apply).
Such sites include blogs, gaming sites, social media, and super-encrypted email platforms.
In fact, Purchase items that are tough to get otherwise
Some common pain relievers and sleeping illegal available in the EU are pills in various Middle East and Asia countries. The dark web comes to the rescue in such cases.
Many turn to the dark to grab such medications with its in modern times private and secure networks.
Actually, Buy legitimate goods secretly
Interestingly, DarkWeb “marketplaces” guarantee confidentiality and anti-surveillance for your online purchases that you simply won’t discover.on any other websites
Swap facts in countries that censor the web
Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet information promoting political dissent. The Darknet offers a place of without charge expression where not even a chunk of these limitations exists.
Revealing the abuse of authority
In fact, The dark web allows political activists and media persons to overview stories that may cause them problems with governments or dictatorial regimes, seeking to infringe on a person’s right to confidentiality.
What should I be as a matter of fact wary of?
Being the unregulated part of the online, the dark web is full of illegal activities. The chances of opening websites with malicious, inappropriate, or illegal information are very high, especially if you don’t know the exact .onion site you wish to visit. Here are some of the potential dangers of the dark web.
- Malware: The dark web contains malicious files and links that can steal your data or compromise your device. This includes ransomware, trojans, and spyware disguised as legitimate files. You may also encounter phishing and social engineering attempts.
- Visits to extreme content: You can encounter extremely inappropriate content such as radical terrorism forums, child pornography, and abusive content. Participating in such forums or downloading such content may lead to investigations by authorities.
- Scams: Almost everyone on the dark web is trying to make a quick buck. This is why you will find people promising to sell you anything only to become a scamming victim.
- Illegal marketplaces: The dark web marketplace has no limits. This is where people sell all types of goods and services like malware, stolen information, counterfeit documents, weapons, drugs, hacking services, etc. Be wary of these underground markets because authorities can track and prosecute you.
Is it to illegal employ Tor?

Interestingly, No, Tor is not strictly illegal to utilize. Journalists activists, and, individuals It is designed to provide online anonymity and confidentiality to its users.concerned about online privacy and security often use it.
Many people employ Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities. , Similarly, peopleActuallyin countries with strict internet access and usage regulations Interestingly, must utilize Tor virtual or clients private networks (VPNs) to access some public websites.
However, while using Tor itself is not illegal, some illegal activities can occur through the network, such as the distribution of child pornography or the sale of illegal drugs. ’s important to note that engaging in illegal activities is still illegal, even through the TorItnetwork.
Also, it is worth noting that using Tor may draw attention from authorities if they suspect you are engaging in illegal activities or if your online behavior raises suspicion. Generally, it’s important to employ Tor responsibly and in accordance with local laws and regulations.
In fact, Are dark websites illegal to apply and visit?

The as it turns out dark web is a controversial internet portionIndeed, often associated with ‘Secret activities.’ While accessing it is carry illegal, it may suggest that a person is attempting to not out an activity that they cannot do publicly.
Anonymity on the dark web may be attractive to government critics and victims of harm who want to keep their identities private. Interestingly, However, criminals and malicious hackers also use the dark web to hide their illegal activities.
Although browsing the dark web is not illegal, it contains unsavory activities that can expose you to danger. Indeed, Remember that any site engagingweaponsin illegal activities such as drug trafficking, sales, hacking, and human trafficking violates international laws and, therefore, is illegal.
How toonaccess the Dark Web Android
You can access the dark web using your Android device by following a few steps. It is highlyalladvisable to take the necessary security measures discussed in this article to protect yourself. Follow these steps to access the dark web on Android:
- Subscribe, download, and install a reliable VPN like NordVPN.
- Download and install the official Tor app from the Google Play Store.
- Login to the VPN client and connect to a server of your choice.
- Open the Tor browser and start exploring the dark web.
How to access the Dark Web on an iPhone
Follow these steps to access the dark web with your iPhone: Actually, The Apple Store does not have an official Tor software. However, several unofficial Tor apps get the position done.
- Subscribe to a reliable VPN like NordVPN.
- Download and install a secure dark web browser for iOS.
- Login to the VPN client and connect to a server of your choice.
- Launch the Tor browser and start exploring the dark web.
. over VPN vsTor VPN over Tor

Visiting the dark web without a VPN or Tor is never as it turns out wise.
But which is better than the other? Interestingly, That’s the question that most folks ask each time they want to jump into the dark world of the web.
While from another perspective the two are similar, a VPN emphasizes secrecy, and Tor emphasizes anonymity.
On its line, a VPN encrypts all your web traffic that travels to (and from) your device and then routes it via a server in your preferred location. Therefore, when combined with TOR, it adds security and anonymity.
So, what about Tor over Virtual Private Network (VPN)?
VPN you join to a When and fire up your Tor Browser, you use Tor over VPN, the most commonly used method. The cyberspace traffic travels to the VPN server first and then bounces into the Tor (The Onion Router) network before reaching its destination. This means that the ISP or any other big brother online will only see the encrypted traffic of the VPN but won’t recognize you using Tor.
As you may know, All you need to do is have a trustworthy VPN providerYou should when using Tor over VPN, as the provider can store metadata logs even if it doesn’t see your explored text.choose a VPN that doesn’t store your logs ( bothtraffic and session), preferably NordVPN or ExpressVPN.
It’s worth noting that Tor over VPN doesn’t protect you from the malicious Tor exit nodes (a final relay before the traffic gets into the destination website) as Tor nodes are merely made of volunteers, most of which don’t play by the rules.
The exit node decrypts traffic, meaning it from another perspective can steal personal details or even inject malicious code. Also, Tor exit nodesare usually blocked by most websites that do not trust them. Plus, Tor over VPN has no power over that.
What about VPN over Tor?
VPN over Tor is less popular than Tor over VPN, and in fact, only two VPNs ((BolehVPN and AirVPN) offer the offering, although none of them is good in terms of rate.
In VPN over Tor, your online traffic moves through the Tor (The Onion Router) network first and then via the VPN. Therefore, it means that yournodesVPN provider cannot access your IP address, but the VPN offers protection against bad exit .
Unfortunately, with this option, your ISP will see that you’re using Tor, which understandably makes it not the recommended pick among the two (Tor over VPN and VPN over Tor).
In VPN over Tor, your faith should be in your Internet Solution Provider, not the VPN provider. Some . consider it in modern times more guarded as they think they can act against their ISPs better if anything goes wrongwill
However, experts recommend Tor over VPN for the possible dark webleadingsafety.
Watch out; Tor ISP could see you using the your

The online providers and websites can still see that you’re using Tor as Tor node IPs are public.
While a web page can’t identify you or an ISP can’t decrypt your web traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions.
Tor BridgesIndeed, or a VPN will guide you to employ Tor privately, as your ISP (Web System Provider) will not see that you’re connected to a Tor node.
So, if you aspire to employ Tor privately, you can apply VPN or Tor gateways (Tor nodes that are not publicly indexed).
Setting up Tor Bridges is merely extra work; you would needIT knowledge, too.
So it is always better to just subscribe to a VPN like ExpressVPN it utilize and with Tor (remember to link to your VPN first and then turn Tor on).
What can my ISP see?
Your Web solution , or ISP, isprovideryour gateway to the Online. Everything you do online goes through your ISP.
It means unless you use a VPN that encrypts your internet traffic, they always receive all information about you and your digital life.
Your Internet Service Provider will see everything when your online data is not encrypted. Your ISP sees what websites you visit, what you do on social networks, your emails, etc.
Sometimes, they even know more than you would like about private matters, such as your health or finances.
This is one of the reasons why it is always togood With all this facts, your ISP could build a very accurate as it turns out account ofandyou link it to your IP address.hide your IP address.
Indeed, Subsequently, most countries have laws on details retention. Indeed, These laws mark how long ISPs must preserve the information they collect.
Such legislation differs by country: in some places, the period is six months; in others, it is at least one year.
During that period, on top of the risk of accidental disclosure and theftInterestingly, , governments and as a matter of fact the police could ask ISPs to share information.
If that happens, you can guess what happens to your information then.It is likely to differ by each provider and, again, by country. Interestingly, Howeverit, is often prohibited for ISPs to offer your facts to third parties.
The encrypted facts, such as WhatsApp messages, are secured behind end-to-end encryption and are not visible to your ISP.
If you want in the EU and live to know what facts your provider has collected about you, the GDPR gives you the rightIn fact, to request a full summary.
Popular dark web criminal cases
Indeed, Deep down, the tip of the iceberg is where over 90% of the cyberspace information is. As much asalongsidethe dark web is supposed to promote gratis speech bypassing censorship, many shady activitiesActually, occur there.
Many high-account stories have shown up due to the press focusing on the dark web, and in from another perspective recent years, several criminal casesbeenhave thrown into the table. Actually, Some of them include:
The Playpen Case
The site had only been up and running for about seven months, but surprisingly, it gained over 215,000 users. The child pornography site Playpen is one of the famous scenarios that resulted from the dark in modern times web.
Then, a law enforcement agency (still unidentified) provided information to the FBI that later accessed the site’s host server.
The FBI didn’t shut the site down but either hosted it for about two weeks, during which they captured over 1,300 IP addresses of site visitors, which led to over 900 users being arrested, including the creator of the site Asyou may know, , Steven Chase.
Silk Road
Silk Road: A cautionary tale about the dark side of the dark web
Silk Road that a black web marketplace was Ross UlbrichtIt was known for facilitating the sale of illegal drugs, goods, and services using Bitcoin cryptocurrency. created between20132011 and . He ended up with over 1.2 billion dollars worth of deals involving firearms, drugs, counterfeit cash, hacker tools, and hits.
Following its popularity, the marketplace in modern times attracted GBI, IRS, and other government agencies’ attention, leading to Ross’ arrest in 2013 and later . imprisonment for his role in operating Silk Roadlife
AlphaBay
It’s notingworththat Just after Silk Road was shut down, AlphaBay became the major marketplace on the dark web.
After its founder, Alexandre Cazes, used the actual email address on the site for communications, reused the same pseudonym on and off the dark kept, and web various unencrypted crypto wallets always open, AlphaBay in modern times was shuttered in 2017.
Indeed, A series of security missteps had led them closer to the extent him even when the cops busted into that, he was logged into the site as “administrator.” Days after the arrest, he was found dead in his cell, allegedly dying by suicide.
It’s worth noting that The Ashley MadisonCase
The dating site Ashley Madison was busted by a hacker group and the impact group in 2015, whereby the hackers threatened to release the consumer’s personal information unless the site and in modern times its sister site, Established Men, were closed.
Since their deadline wasn’t met for facts closer of the sites a month later, the Impact organization ascended to the dark web, where they started to publish the the.
Over 32 million IP addresses of members were released, including that of the site’s CEO, with hackers claiming that the site had obliged its primary more than ever purpose and that they were forcing members to pay from get their accounts deleted to the site.
Actually, We have discussed the most scandalous dark web cases in this article in detail
Your can end up landingdetailsanywhere
Since events like Wikileaks and informants such as Edward Snowden have revealed that several authorized institutions frequently spy on citizens worldwide, confidentiality has become an often-discussed topic.
a As matter of fact, your data could be anywhere on the internet, meaning it could already be at the three internet levels (surface web, deep web, and dark web).
The chances are that you have already a presence on the clear web (the surface web), be it a LinkedIn user info, social media, Facebook, or any community involvement.
Also, your information is more likely on the deep cyberspace in one way or the other. But you have to keep your fingers crossed that it remains there and hope the party holding your facts (the school or hospital records department) keeps it according to the GDPR standards.
web cloud is another channel that has fueled the growth of the deep The. In fact, For instance, if a cloud storage firm like Dropbox gets its files on the Amazon web server, your facts is already placed in modern times on the deep web.
It should not be a confidentiality issue unless the business gets hacked or your information is exposed accidentally.
Keep in mind, at any given time. You could be followed online by different groups and things such as in modern times :
- Internet service providers (ISP)
- Operating systems
- Your network administrator (Wi-Fi)
- Internet browser
- Apps
- Hackers
- Websites
- Governments
Can I get rid of informationmyfrom the dark net?
Removing your personalsensitiveinformation from the Dark Web once it has been exposed is virtually impossible. This irreversible process highlights the importance of taking preventive measures by utilizing a platformforthat monitors your facts potential breaches.
Consider changing your usernames and passwords as from another perspective an additional security measure.
What can I do if more than ever my personal information is on the dark web?
If your personal information has been leaked on the Dark Web, your risk of identity theftThis is why many people prefer an identity theft protection offering and a Actually, and financial fraud significantly increases. financial and credit fraud protection solution. Interestingly, By doing so, early signs of fraud can be detected in near-real time, such as recent inquiries on your credit document like fresh credit cards or bank loans.
More dark web safety tips
Actually, By immediately, you should know how to access the dark web safely and anonymously using a VPN and Browser Tor the.
But still, there’re some other tips you can employ to bolster your dark web securityBelow, I will list them for you: once commence you your journey into the Darknet.
Adjustsettingthe Tor security
Tor provides you with an inbuilt slider to let levels tweak the security you. You only need to tap on the onion emblem and select Security Settings.
You can , adjust the slider to a point when the cursor points to the safestthenmeaning the JavaScript will be disabled on all websites you visit by default.
Actually, Please note some images as it turns out and symbols might not display after you set your Tor security configuration to the safest.
Actually, Rescale or minimize window Tor browsing the
Most people aren’t aware that you can be tracked depending on the dimensions of your active window.
Therefore, as much as it’s a tip that sounds rather off, you should ensure that you minimize your Tor window before you proceed.
Shut down Tails
Don’t make mistakes at the more than ever tail-end of surfing the dark web by forgetting to close the tails.
Always remember to shut down the tails because once they get shut, the drive, for instance, will wipe itself from the thumb OS you installed.




